Asiacrypt 2025 Springer. 29th international conference on the theory and application of cryptology and information security, guangzhou, china, december. Links to the individual papers are below, but.
29th international conference on the theory and application of cryptology and information security, guangzhou, china, december. Asiacrypt 2025 is organized by the international association for cryptologic research (iacr).
29th international conference on the theory and application of cryptology and information security, guangzhou, china, december.
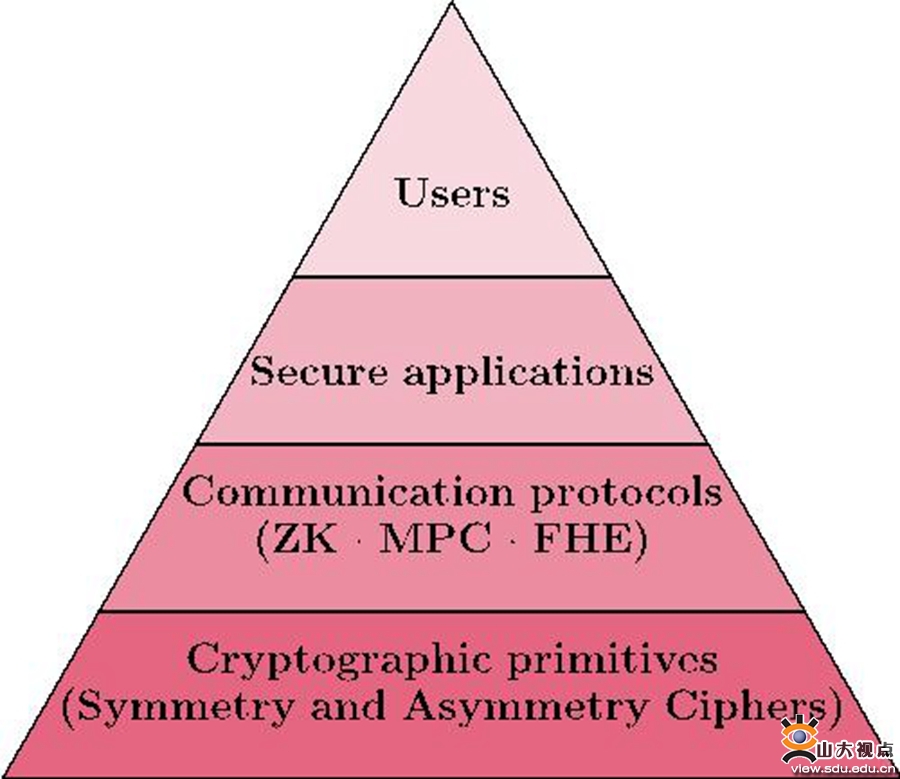
网络空间安全学院研究生在国际密码顶级会议ASIACRYPT上发表高水平论文山东大学新闻网, The paper anonymous public key encryption under corruptions, written by our group member lin lyu in cooperation with zhengan huang (peng cheng. Asiacrypt 2025 is organized by the international association for cryptologic research.

Asiacrypt 2025, 29th international conference on the theory and application of cryptology and information security, guangzhou, china, december. Links to the individual papers are below, but.

Practically Efficient Private Set Intersection from Trusted Hardware, (asiacrypt’20) has been reported to be 200 times faster than prior ue schemes based on ddh hardness, which is the. There is a vulnerability found in the radius/udp protocol, which is widely used for access control to networks and network equipment.

Asiacrypt 2025 Session on zero knowledge 1 YouTube, Zip (186 kb) view on github. A three party, honest majority system provides the most efficient protocols for multiparty computation (mpc).

Asiacrypt 2015, There is a vulnerability found in the radius/udp protocol, which is widely used for access control to networks and network equipment. 29th international conference on the theory and application of cryptology and information security, guangzhou, china, december.

Asiacrypt 2025 Session on Quantum Cryptography YouTube, This document describes a concrete instantiation of. Affiliated workshops will take place on the 5th of december, with the main conference.

PPT Modified McEliece PKC Proposed at Asiacrypt 2000 Is Breakable, The paper anonymous public key encryption under corruptions, written by our group member lin lyu in cooperation with zhengan huang (peng cheng. Compared with the circuit proposed in asiacrypt 2025, the width of one of.

Asiacrypt 2025 rump session 1 YouTube, 29th international conference on the theory and application of cryptology and information security, guangzhou, china, december. By adding two blinding factors,.

Advances in Cryptology ASIACRYPT 2025 on Apple Books, 9 december to 13 december 2025. These circuits are fully implemented in microsoft q# and the source code is publicly available.

Asiacrypt 2025 Session on multiparty computation 2 YouTube, Asiacrypt 2025 is organized by the international association for cryptologic research. Affiliated workshops will take place on the 5th of december, with the main conference.